What Is Cyber Security And Why Is It Important?
Posted on February 17th, 2023 by Nico Prins in Security, Explainer
In an online age, cyber security is more crucial than ever. It is essential to do business, socialize, and store sensitive information. It is crucial to stay secure online. Whether it's ransomware, phishing emails, or data breaches, countless potential sources of attack can have huge implications and expensive consequences.
Internet in Numbers 2022
Posted on February 14th, 2023 by WebSitePulse in Industry News, Statistics
“The Internet (or Internet) is the global system of interconnected computer networks that uses the Internet protocol suite (TCP/IP) to communicate between networks and devices. It is a network of networks that consists of private, public, academic, business, and government networks of local to global scope, linked by a broad array of electronic, wireless, and optical networking technologies. The Internet carries a vast range of information resources and services, such as the inter-linked hypertext documents and applications of the World Wide Web (WWW), electronic mail, telephony, and file sharing.” — Wikipedia.
Getting More Web Traffic? How to Prepare Your Site for Large Scale Traffic
Posted on February 3rd, 2023 by Matthew Cooper in Guides
It can be challenging to understand the specific factors that can cause traffic to surge on your website. Sometimes, there are temporary spikes, usually related to sales or special events, and other times, this increase in traffic can be permanent. Website owners should be ready to handle large volumes of visitors as any breakdown, no matter how short-lived, can cause you to lose potential business.
Understanding the 3-2-1 Backup Rule
Posted on January 18th, 2023 by Joshua Smith in Security, Explainer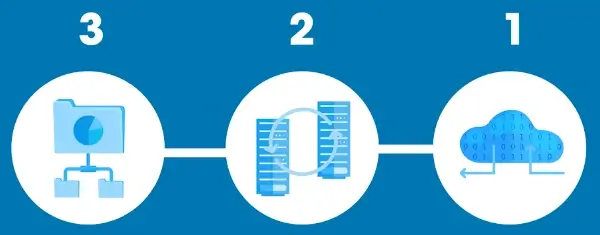
While data disasters are inevitable, having a planned backup strategy can mitigate its damaging effects. According to the Cybersecurity and Infrastructure Security Agency, businesses and organizations should observe the 3-2-1 backup strategy for assured data safety.
3 Types of Access Control: IT Security Models Explained
Posted on January 4th, 2023 by Nicole Kelly in Security, Explainer
If you watched Mission Impossible: Rogue Nation, you probably remember the infamous Gait Analysis access control system. After the agent passes the main gate, enters the elevator with fingerprint recognition, and opens three unique-combination locks, he goes through a camera-based system that recognizes how he walks, talks, and moves his face.

 Copyright 2000-2024, WebSitePulse. All rights reserved.
Copyright 2000-2024, WebSitePulse. All rights reserved.