9 Smart Ways to Keep Customer Data Secure on Your E-Commerce Website
Posted on September 24th, 2020 by Jake Rheude in Guides, Security
E-commerce has now revolutionized the way that people shop. But one of the biggest challenges a lot of e-commerce owners face today is website security.
11 Different Types of Spoofing Attacks to Be Aware Of
Posted on February 14th, 2020 by David Balaban in Lists, Security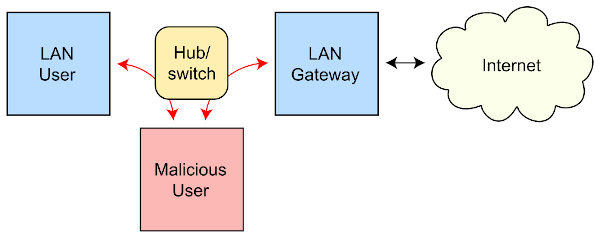
In terms of cyber-attack vectors, spoofing is exactly what it sounds like. This term embraces a series of techniques aimed at masquerading an attacker or electronic device as someone or something else to gain the victim’s confidence. Whether it is used to deceive a user or to manipulate a computer system, this multi-pronged phenomenon is often at the core of social engineering hoaxes in general and phishing campaigns in particular.
How to Prevent a Content Theft from Your Website
Posted on November 28th, 2019 by Dmitry Leiba in Guides, Security
Web content is being stolen, and that's a trend. In 2013, Google employee Matt Cutts said that 30% of content on the Internet is plagiarism. 6 years have passed, and the situation has not improved. Despite the emergence of a new source determination algorithm in Google, hundreds of thousands of users copy other people's photos, videos, and texts to present them as their own. We'll tell you how to protect content from theft and adequately respond to plagiarism.
Why Do Websites Get Blocked and How to Bypass it
Posted on August 1st, 2019 by Natalia Diatko in Guides, Security
Censorship appears to be increasingly severe not only in countries we traditionally view as authoritarian (Iran, North Korea, China, Russia, etc.) but also in Western ones. It is not uncommon anymore for users from around the globe to find themselves unable to access their favorite resources.
15 Things Online Businesses Need to Know About Web Security
Posted on May 15th, 2018 by Shahid Mansuri in Guides, Security
Web security for online businesses is not very well understood by many. The influx of content managing systems has led to a lot of online presence that is confused about how online security works. Some people who use these CMS do not know what web security is and how to implement it.

 Copyright 2000-2025, WebSitePulse. All rights reserved.
Copyright 2000-2025, WebSitePulse. All rights reserved.