In terms of cyber-attack vectors, spoofing is exactly what it sounds like. This term embraces a series of techniques aimed at masquerading an attacker or electronic device as someone or something else to gain the victim’s confidence. Whether it is used to deceive a user or to manipulate a computer system, this multi-pronged phenomenon is often at the core of social engineering hoaxes in general and phishing campaigns in particular.
The crooks’ objectives range from gaining unauthorized access to one’s system and personal accounts – to stealing money and distributing malicious software. Spoofing attacks are heterogeneous and come in quite a few different forms. This article covers the common types of these plots to help you identify them and keep your digital life from being a low-hanging fruit for criminals.
1. ARP spoofing
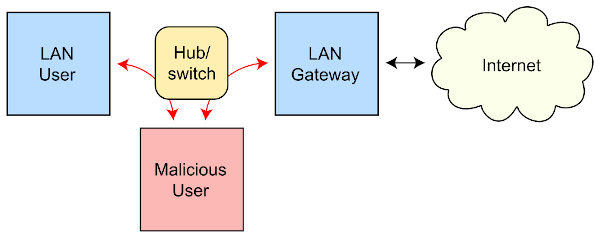
For the record, ARP stands for Address Resolution Protocol, a communication mechanism used to map an IP address to a specific machine's physical (MAC) address within a local area network. An ARP spoofing attack aims to link a criminal’s MAC address with a dynamic Internet Protocol address of a target host. It results in rerouting all traffic intended for the victim’s IP address to the attacker. In addition to intercepting network data, the malefactor can alter or even halt the traffic.
2. MAC spoofing
This technique revolves around modifying the Media Access Control (MAC) address of an Internet-facing device to impersonate it. Although the MAC address is uniquely assigned to every network adapter and is supposed to be immutable, some network interface controller (NIC) drivers allow it to be altered. This inconsistency is a source of attacks where a malicious actor’s computer mimics a machine on a target network. The goal is to circumvent regular access restrictions on a server or router level so that the attacker can pose as a trusted user and thereby perpetrate scams or gain a foothold on the network.
3. IP spoofing
IP spoofing is a malicious technique that relies on generating Internet Protocol (IP) packets with a fabricated source address. By executing such an attack, cybercriminals can cloak the original details of the packet sender and thus forge the computer’s networking “identity.” This method can be leveraged to veil the real source of a DDoS attack and make the corrupt packets harder to filter, given that each one appears to stem from a different address. Another use case is to bypass authentication methods based on IP addresses.
4. DNS spoofing (DNS cache poisoning)
Domain Name Server (DNS) is an entity that maps domain names to IP addresses, making the web surfing routine user-friendly. In other words, it allows you to visit sites by typing their URLs in the browser rather than random-looking IP strings that are nearly impossible to memorize. Cybercrooks may harness vulnerabilities in a DNS server to tamper with its cache and thus fraudulently impose invalid associations between domain names and IP addresses. This way, the victim’s traffic can be rerouted to a faux website that looks just like the original one.
5. Email spoofing
This mechanism comes down to altering email sender details visible in the “From” field so that the message appears to have been sent by somebody else. Email spoofing allows an attacker to pass himself off as a person you know and trust, such as a colleague, business partner, or family member. Scammers use email spoofing attacks to dupe you into visiting a phishing site that requests sensitive information or spreads viruses under the guise of important software updates. This scheme is also the central element of CEO fraud, where employees in an organization’s finance department receive spoofed wire transfer requests that appear to come from senior executives.
6. Website spoofing
Social engineering frauds often cash in on replicas of certain sites you visit a lot. A rogue web page imitates the look and feels of its legitimate counterpart, copying the design, branding, login form, and in many cases, even the domain name via the above-mentioned DNS cache poisoning trick. Website spoofing typically works in tandem with email spoofing so that the victim is redirected to the forged page by clicking a link in a bogus email. The crooks’ goal is to wheedle out your authentication details or deposit dangerous code onto your machine through drive-by downloads. URL\website spoofing may also lead to malware infections or even identity theft.
7. Caller ID spoofing
Scammers may falsify the caller information shown on your phone’s display to mask the actual origin of the call. To this end, they exploit imperfections in the way some telco equipment handles the caller name display. This attack makes it look like the call is coming from your area or even from your neighborhood. In some scenarios, caller ID spoofing causes a trusted company’s logo and address to be displayed in the call details so that you are more likely to answer the phone. The objective is to convince you to give away personal information or pay for services you never opted for.
8. Text message spoofing
Also referred to as SMS spoofing, this social engineering vector is used by fraudsters to send text messages on behalf of another person or company you have some relationship with. The logic of the attack is all about misrepresenting the sender ID or phone number so that you believe that the text message comes from a trustworthy individual or organization. The SMS will typically include instructions to follow a link (you guessed it – a malicious one), which is leveraged as a launchpad for phishing.
On a side note, this form of spoofing isn’t necessarily carried out for shady purposes. Many businesses use the appropriate technology provided by mobile carriers to replace a regular phone number with an alphanumeric string associated with the brand.
9. GPS spoofing
The idea behind a GPS spoofing attack is to deceive an electronic device’s geolocation module into reporting the wrong whereabouts. At first sight, the aim of this exploitation might seem vague. However, there are a few potential uses that make this tactic increasingly disconcerting. Imagine the navigation system of a boat receiving wrong GPS coordinates and causing the vessel to head in the wrong direction – the consequences can be devastating.
Aside from physical injury, sabotage, cyber-warfare, and suchlike terrifying things, the motivation for executing this attack can be quite innocuous. Fans of location-aware mobile games such as Pokémon GO may want to spoof GPS data for cheating. This technique underlies a foul play where a gamer makes their device think it’s close to an outdoor “gym” while the person is comfortably sitting on a couch at home.
10. Extension spoofing
This technique allows malware operators to camouflage dangerous executables as benign files. Here’s the thing: to ensure proper user experience, Windows operating system hides file extensions by default. That being said, an object named “Photo.jpg.exe” will look just like a regular image unless you manually configure your system to show extensions. As a result, cybercriminals can disguise malware binaries as objects that don’t raise any apparent red flags. Fortunately, most antivirus tools easily identify such infection attempts, and therefore you should be safe as long as you are using an effective security solution.
11. Facial spoofing
As authentication practices are evolving, face recognition systems may become ubiquitous soon. We are accustomed to using face ID features for unlocking our mobile devices and laptops. The chances are that this form of biometrics will supersede the current payment authorization and document signing methods down the road. Scammers will try to find their way around this security paradigm. As a matter of fact, researchers have already demonstrated a proof-of-concept where 3D facial models (based on one’s photos from a social network) fooled several mainstream authentication systems. Well-motivated evildoers can definitely do the same.
How to stay safe from spoofing attacks
Now that you have familiarized yourself with the most widespread types of spoofing attacks let’s see how you can fend them off. Here are a few best-practice tips in this regard:
- Enable your spam filter. This will block most phishing emails, including ones with spoofed sender details.
- Refrain from clicking links and opening email attachments if you don’t know who the sender is. In case the email appears to come from a familiar source but looks suspicious, you are better off contacting the purported sender in some other way to ascertain that the information is trustworthy. A quick phone call will do the trick.
- Examine emails for typos and grammar errors. These inaccuracies in an email subject and body can be a giveaway in a phishing scenario.
- Avoid non-HTTPS sites. If a legit-looking email or text message instructs you to click an embedded link, make sure the site uses a secure communication protocol before entering any information in it. If the URL starts with “HTTP” rather than “HTTPS,” you are most likely dealing with a spoofed website lacking an encrypted connection.
- Make file extensions visible. As previously mentioned, Windows obfuscates extensions unless configured otherwise. To avoid the double extension trick, click the “View” tab in File Explorer and check the “File name extensions” box.
- Use a reliable Internet security tool with an anti-phishing module on board.
- Check your network for loopholes. If you run an online business, keeping tabs on potential weak links in your IT ecosystem will give you actionable insights into what needs improvement. A great way to harden your defenses is to use a Network Vulnerability Monitoring service. It will inspect your servers for thousands of known exploits, security flaws, and malware strains, additionally providing recommendations on how to take your security posture to a whole new level.


 Copyright 2000-2025, WebSitePulse. All rights reserved.
Copyright 2000-2025, WebSitePulse. All rights reserved.