 Have you ever wondered whether you have configured your servers and firewalls properly and according to the latest security standards? Are you aware of the new exploits that can harm your system and the available updates that will secure your applications and servers?
Have you ever wondered whether you have configured your servers and firewalls properly and according to the latest security standards? Are you aware of the new exploits that can harm your system and the available updates that will secure your applications and servers?
Vulnerability monitoring can give you a peace of mind regardless of how secure your servers and firewalls are.
The biggest advantage of our vulnerability scan is that you do not have to install any software on your side. By simply entering a domain name or an IP address, you will get a comprehensive security assessment in less than 15 minutes.
We are able to check basically all operating systems: Windows, Mac, Linux, Solaris, BSD, Cisco iOS, IBM iSeries. The different tests are updated daily and when new vulnerabilities are found, they are added and tested for.
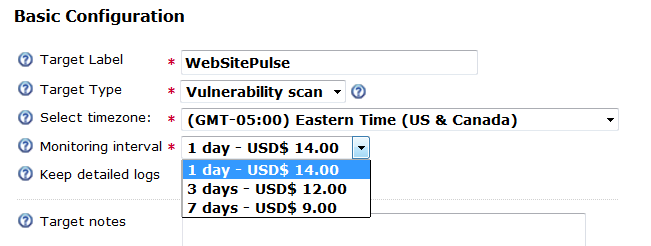
You can choose to run these tests every 1, 3 or 7 days, and if new problems are discovered, you will be alerted immediately.
By looking at the report, you will be able to identify the issues you have with your system and take steps to fix them quickly. This will lower your risk of unwanted attacks and also help you avoid potential compliance and audit problems.
Databases are always at risk and we are able to test most of them for potential problems: Oracle, SQL Server, MySQL, DB2, etc. Web applications are also tested for vulnerabilities (web servers and web services).
In addition, we can detect compromised systems. We scan for most known backdoors, viruses and malware that leave your system vulnerable to attacks form outside your network.
The generated report identifies the security problems and provides you with information how to fix them. Also it will show warning of potential risks and other details.
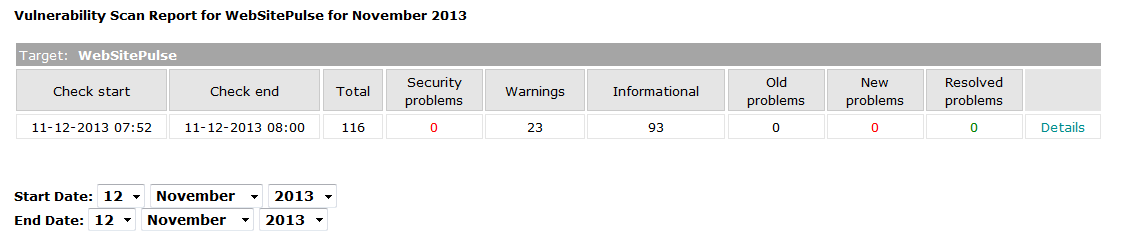
Here is an example:
This is the summary report for a web site and it shows that there are not any security problems detected right now. Still, there are 23 warnings that the administrator of the website might want to look at.
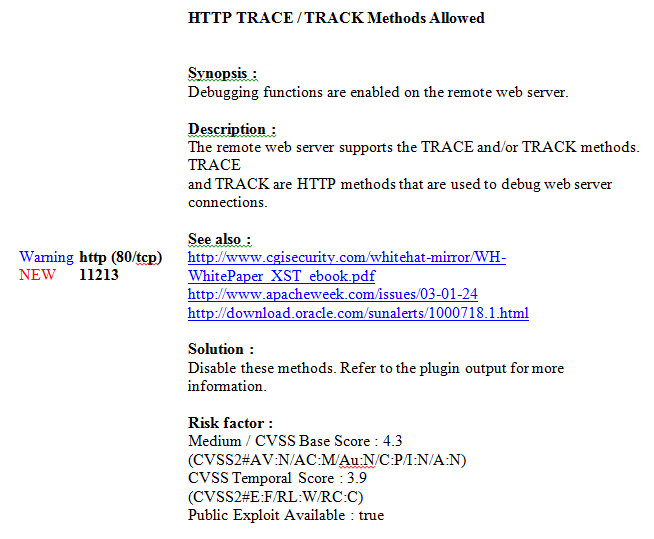
By following the details link, I got the following information:
These are the details for just one of the warnings we have detected.
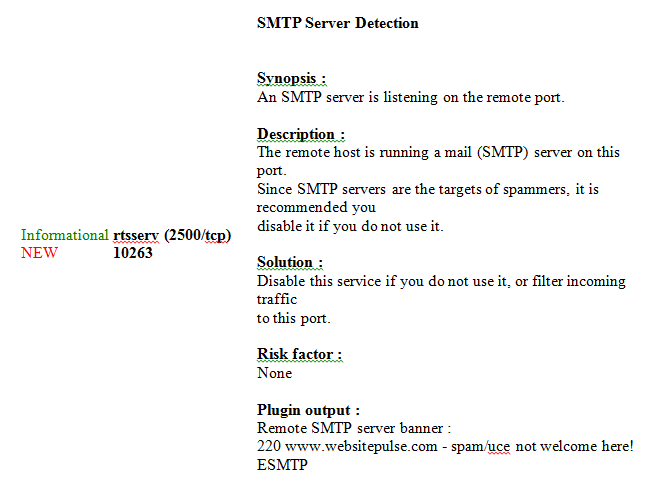
There are also informational details that look like this:
As you can see, this level of monitoring can be very useful to any administrator in finding and identifying potential security risks and vulnerabilities.
The synopsis and description details provide you with additional information regarding the service in question. The see also and solution sections provide you with possible ways to resolve the problems in case of security problems or warnings.
The tests we run, are very accurate and we have tried to minimize the false positive results. The deployment is simple and does not require any maintenance on your side.
To create a vulnerability monitoring target, simply go to Targets –> Create New Targets –> Security and Blacklist Monitoring and choose vulnerability scan.
Next, we will look at Blacklist monitoring, which is also a useful tool for all system administrators.


 Copyright 2000-2025, WebSitePulse. All rights reserved.
Copyright 2000-2025, WebSitePulse. All rights reserved.