
We rely heavily on our networks for business continuity. As technology evolves, we can do so much more. At the same time, increased complexity makes it challenging to keep track of everything. Reaching and maintaining network visibility sometimes feels like chasing the carrot at the end of the stick.
Table of Contents:
What is Network Visibility?
Why is Network Visibility Important?
Challenges to Network Visibility
Network Visibility Best Practices
Conclusion
When discussing visualizing the network, we don't mean staring endlessly at green characters scrolling vertically. We're talking about knowing what's happening in your network and who's using it.
This guide will explain how to achieve network visibility for your organization.
What is Network Visibility?
Network visibility observes your network infrastructure from end to end. It looks at all relevant components, including connected devices, virtual environments, applications, and end users, and the data that flows between these sources.
Visibility doesn't care about using CRM vs CDP to collect customer data. It's only concerned with monitoring and controlling where that data flows.
The aim is to understand every part of your network and what "normal activity" looks like so you can make efficiency improvements while safeguarding against security threats.
Why is Network Visibility Important?

Achieving network visibility takes a massive, coordinated effort, but it's worth the investment.
Daily business activities are moving further into digital spaces, so you're at the mercy of your network and its infrastructure. Why wouldn't you want a way to monitor network performance and incidence?
Let's dig deeper into some of the reasons to prioritize network visibility.
Cybersecurity
According to IBM, the global average data breach cost rose to $4.88 million in 2024.
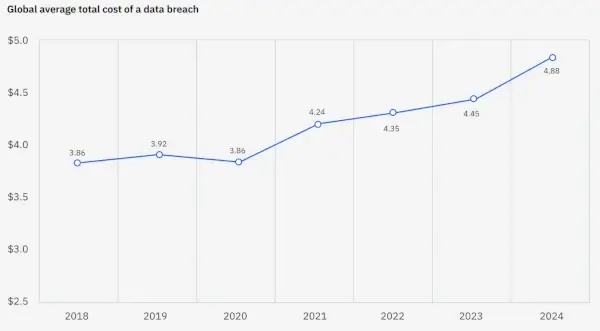
Breaches are one of many ways hackers can damage your network (and business). They can also break websites, switch servers, and take your application services down.
Greater network visibility allows you to be proactive by observing data flows in real time and taking action as soon as you identify a weakness.
Threat Identification
Malware and other threats will attempt to penetrate your network. If and when they do, network visibility tools quickly identify the issue. Knowing what you're dealing with is half of the battle.
Identify Blind Spots
Despite best efforts, every network has hidden vulnerabilities. Network monitoring helps you compile historical data and establish baselines for what's expected. Irregular trends and patterns highlight areas at risk for intrusion.
Troubleshooting
Discovering the root cause of problems is easier when you're already observing them as they occur. You'll reach solutions faster, mitigate threats, and reduce network or website downtime. That means you reduce losses, maintain business continuity, and keep customers happy.
Improving Network Performance
Network visibility means better visibility of the flow of data vertically and laterally. This produces insights for optimizing bandwidth and handling traffic to eliminate bottlenecks and increase end-user responsiveness.
Compliance
Data privacy and protection laws demand documentation and traceability for sensitive customer data. If you're monitoring your network, you'll have instant access to network data to account for what information was exposed and when.
Better Planning
Monitoring and analyzing network data provides insight into the health of the overall network. By getting ahead of problems such as aging and legacy business apps or overloaded CICS mainframes, you can then replace hardware and software before it's too late and maintain business continuity.
Challenges to Network Visibility
Complete network visibility requires handling many variables plus swathes of data. So, it's important to be aware of what challenges you need to navigate.
- Remote access. Owl Labs reports that 38% of workers are hybrid or fully remote today. While remote work has many benefits for employees and businesses, it can make visibility tricky. Users often connect to business systems on Virtual Private Networks (VPNs) that offer encryption but prevent standard monitoring and limit traffic visibility.
- Network complexity. As more network resources shift to the cloud, the need for cloud security reduces visibility. Internet of Things (IoT) devices use edge computing, disconnecting data from your network.
- Tool limitations. Each tool has its limitations and blind spots in data collection and analysis. You must use the right blend of tools to cover your bases.
- Data encryption. SSL and other encryption methods are standard practice. While this protects data, it comes at the expense of lower visibility. Hackers will use the same types of traffic encryption to hide their activities in your network.
7 Network Visibility Best Practices
If you want to achieve complete network visibility from day one until long into the future, follow these guidelines.
1. Build Sustainable, Reliable Data Collection

Comprehensive analysis requires you to parse through huge volumes of traffic and flow data. You can't always parse every single byte of information. Instead, you need consistent indicators of network performance and health.
Optimize Packet Access
The smallest bytes of transferred data for analysis are known as packets. You have to capture packets effectively, otherwise, you'll develop blind spots. Work with IT specialists to access and select the best packet types for monitoring.
Picking reliable network slices will help you troubleshoot issues and flag anomalies. Use network monitoring tools that can scale as your traffic grows.
Include Virtual Infrastructure
Today, accommodating cloud and mobile networks and the devices that connect to them is vital. However, virtual environments like cloud-based services, virtual machines (VMs), and software-defined networks (SDNs) obscure traffic.
To counteract this, visibility tools built for cloud-based environments should be implemented. These connect the physical and virtual layers, tracking data as it moves from one virtual data center to another for better visibility.
Deploy Network TAP and SPAN Port Technologies
Test access points (TAPs) provide continuous access to traffic for passive monitoring. Switched port analyzers (SPANs) are used for port mirroring, where packets are copied and sent to your data hubs.
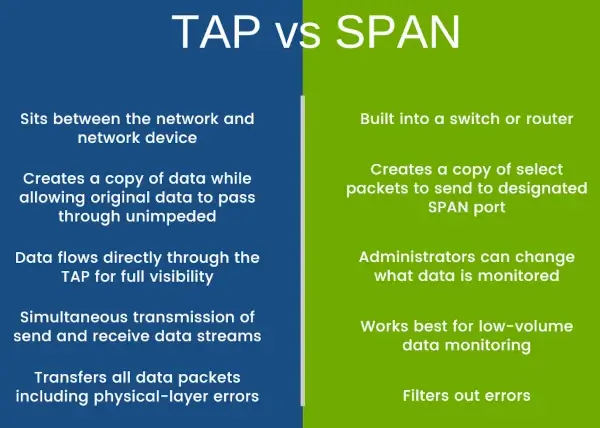
TAPs are simpler to implement, but each one introduces a threat access point. SPANs are more flexible than TAPs but are limited in the amount of data they can monitor. Consider using both for greater adaptability to changing network complexities.
2. Monitor All Network Layers
Your network has several layers, each of which presents possible issues. True visibility incorporates a monitoring process on every layer.
According to the Open Systems Interconnection (OSI) model, there are seven layers in a network:
- Physical layer. The electrical and optical pulses of data transmission to the physical device.
- Data link layer. Data travels node-to-node and is verified, error-corrected, and packaged.
- Network layer. Receives data and progress toward target destinations.
- Transport layer. Protocols such as TCP regulate the transfer of data packets.
- Session layer. Manages connection and exchanges between two devices.
- Presentation layer. Data is translated or converted into information compatible with the application.
- Application layer. Where the end-user interacts, traffic includes usage and clickstream data analysis.
Identify relevant layers and components in your network and establish monitoring protocols for each. For example, IP monitoring is essential for tracking the network layer. Whereas, physical layers often require sensors and in-person testing.
3. Automate Contextual Alerts
Network visibility doesn't help much if you're not alerted to potential problems and traffic anomalies. It's also not always useful for your team to get a simple notification that something in the network is down.
People want actionable information. What's happening and why? Where is the issue located? What's the recommended course of action?
Customize monitoring and threat analysis tools to send contextual notifications. Send these to appropriate team members, giving them a head start to solving network security and performance issues.
4. Use Network Monitoring Solutions
The best way to build visibility is with network monitoring services that automate the process. Many vendors offer various data tracking options.
WebSitePulse provides monitoring for:
- Databases
- Remote services
- Web servers
- VoIP servers
- Email servers
- DNS servers
- Network uptime
Using services like this puts network visibility in the hands of the experts, guaranteeing complete visibility and proactive measures for an added layer of security. It monitors your site 24/7, sending immediate alerts in case of error detection to reduce the risk of lost revenue from network downtime.
5. Prioritize Application Monitoring
For most of your team, particularly if they're hybrid or remote, applications help get the job done. You want to track application performance and ensure people get the necessary productivity boost.
Application performance monitoring (APM) tools track the end-user experience, performance metrics, and availability. In short, they ensure your team can use critical apps for the required jobs. Working apps also mean happier employees.
6. Implement Encrypted Traffic Analysis
Traffic encryption is essential for cybersecurity and compliance. Encrypted Traffic Analysis (ETA) tools such as GREYCORTEX Mendel monitor encrypted traffic without decrypting it, maintaining both security and privacy.
ETA uses metadata, traffic patterns, and machine learning to detect anomalies or threats hidden within encrypted flows.
Other tactics for increasing the visibility of encrypted traffic include:
- Enable and Monitor SSL/TLS decryption. Selectively decrypt traffic to inspect contents.
- Install packet flow switches. Send multiple decrypted copies to different analysis tools.
- Use proxy-based architecture. Decrypt for analysis, then re-encrypt before moving data along.
7. Leverage Remote Network Monitoring
Remote access enables your business to work more flexibly and stay competitive. While it hinders visibility, there are several workarounds you can implement.
Use the following to leverage remote network monitoring
- Cloud-based network monitoring tools. Provide real-time access to network data across the environment.
- Probes and sensors. Deployed remotely to capture traffic data and send it to centralized monitoring.
- VPN and SD-WAN monitoring. Monitor traffic for remote workers connecting to your network.
Secure Your Business With Greater Network Visibility
Your organization will only get as far as your network systems can take you. Don't leave things up to chance, and only react when something breaks.
Improve your network visibility with threat identification tools and monitoring services. This will protect your network and the sensitive information of your employees and customers.
Better visibility also means better control of data flows for greater network performance. Don't put it off until you lose the network. Start building a visibility strategy today!



 Copyright 2000-2026, WebSitePulse. All rights reserved.
Copyright 2000-2026, WebSitePulse. All rights reserved.