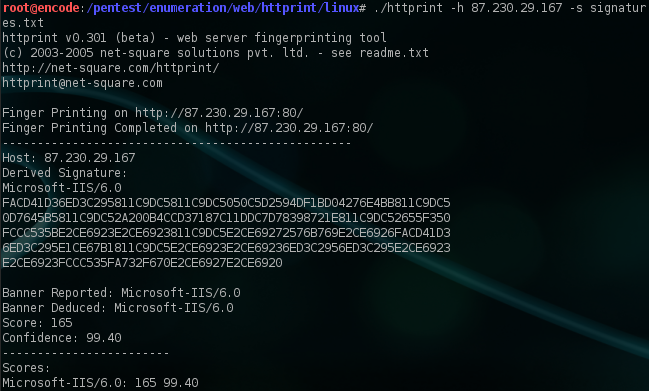
HttPrint is a web server fingerprinting tool by Net Square. It reveals all the details about a web server, and it makes a pretty decent conclusion about what the webserver used. Identification is based on the implementation differences in the HTTP protocol.
In a previous post we have discussed server masking as a way to protect you against crackers and potential threads. This tool kind of goes the other way around. There are two ways to look at it:
- as a weapon for crackers
- as a way for you to make sure that you masked your server properly and there are no giveaways to your doings
HttPrint goes beyond the banner string of a web server and looks at other characteristics before it jumps into conclusions. The tool looks at the HTTP protocol’s behavior and the way it is implemented by the server. This includes HTTP header field ordering, forbidden operation response, improper HTTP version response and improper protocol response.
Another giveaway it notices is the default usage of eTags on some servers. We don’t think they are actually using this as a signal at the moment, but it is a good giveaway. Lighttpd usually has this enabled by default, as for Apache, you need to turn it on manually.
One of the other great features of the tool is the html reports. When will that come useful? Well, when you are running the console version (probably automated) and you would like to see eye-friendly reports in your browser. You will also get the percentage of the results’ accuracy. They use multiple signals, so results might or might not be true, but they will surely be enough to be at least an educated guess.
According to the developers of mod_security, they can successfully fool HttPrint, which to us sounds like a relief. After all, this is mostly a defensive security measure.
If you need your server protected and accurately monitored for any suspicious behavior, drop us a line and we will come up with a great plan, depending on your server monitoring needs.


 Copyright 2000-2025, WebSitePulse. All rights reserved.
Copyright 2000-2025, WebSitePulse. All rights reserved.