
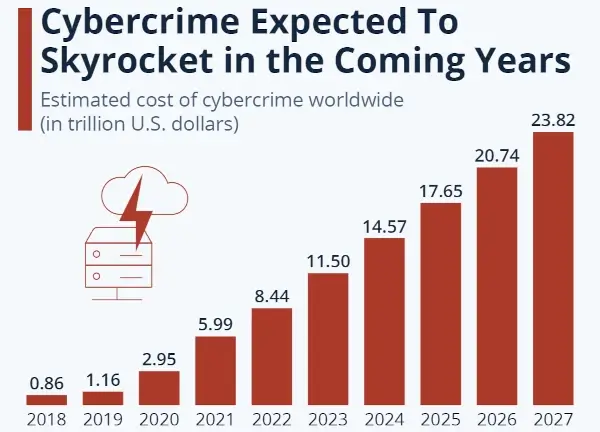
Cybersecurity remains a key concern for any organization. The cost of cybercrime is expected to rise to $8 trillion in 2023 and reach $10.5 trillion by 2025.
Various cybersecurity solutions are available, with Firewall as a Service (FWaaS) emerging as one of the most valuable assets when it comes to protecting your interests.
We will investigate FWaaS solutions, how they work, how they're different from traditional firewalls, and what benefits they can provide for a range of organizations.
What is Firewall as a Service (FWaaS)?
Firewalls are a security feature that inspects incoming and outgoing traffic to determine their authenticity. A firewall will either allow or block traffic based on a set of predefined security rules. They are essentially a barrier between your secured internal network and unsecured outside networks.
Firewall as a Service (FWaaS) is a cloud-based firewall solution, meaning no on-premise hardware is required to run it. It provides all the services of a traditional firewall, including advanced threat protection (ATP), Domain Name System (DNS) security, intrusion prevention system (IPS), and web filtering.
It's important to note that FWaaS can also protect against Domain Name System (DNS) errors, such as the DNS probe finished nxdomain error, which occurs when a domain name cannot be resolved. This is because FWaaS solutions often include DNS security as part of their comprehensive security features.
Additionally, FWaaS solutions can be a valuable tool for organizations looking to improve their cloud hosting security.
Because FWaaS are cloud-based, they can be scaled and molded to the individual needs of the network they're protecting, considering its size, demand, configuration, and unique security needs.
With cybercrime consistently rising year-on-year, firewalls are needed as part of a robust security solution for every organization operating online.
How Does FWaaS Work?
Firewalls enforce the rules set up by network administrators. If somebody on the network tries to access something potentially harmful or a potentially dangerous third party attempts to access the network, the firewall blocks the connection. It then alerts the network administrators.
The firewall will inspect any traffic entering the network and analyze aspects of each data packet, such as the location of origin, to determine if it is safe.
FWaaS operate similarly but are hosted in the cloud rather than being physically installed on-site and connected to internet routers. Access to an FWaaS is often provided through an internet-based administrative panel, which allows for the firewall's configuration, including which URLs and IP addresses are allowed or blocked.
Because management is centralized from a single console, and the firewall is embedded in the network infrastructure, protection can be offered for network users regardless of whatever device or location they're accessing the network from.
FWaaS features are often straightforward to set up, with minimal changes required to router settings and little else. Once the router is connected to the FWaaS provider, traffic will be routed through the provider to detect and address threats.
How Does FWaaS Differ From Other Firewalls?
FWaaS solutions differ from NGFWs (Next-Generation Firewalls) in several ways, despite offering many of the same network protections.
The most obvious difference is that FWaaS solutions are hosted and maintained by a third party, meaning an organization doesn't have to spend time or money maintaining software or hardware to stay protected.
It's also worth noting that most NGFWs were not designed to support cloud applications. This can sometimes lead to being overwhelmed by the high volume of long-lived connections that these applications require.
With the use of cloud-based applications increasing significantly in many organizations, as evidenced by the increasing revenue of cloud providers below, this can present a significant problem.
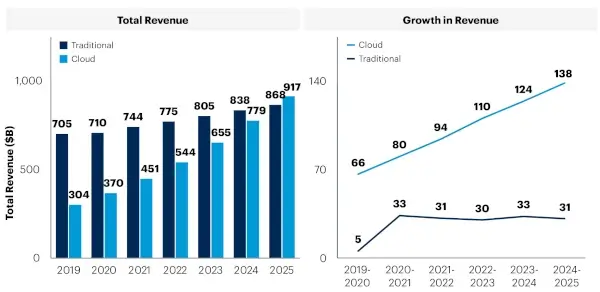
FWaaS often performs faster when using cloud applications, as traffic doesn't need to be rerouted as extensively. NGFWs also often require additional software to process SSL inspections, which FWaaS solutions accomplish natively. This can further reduce performance.
It's also easier to duplicate security architectures across multiple locations with FWaaS solutions. This is important for organizations operating in numerous locations, as it eliminates the need for NGFWs to be set up and configured independently at each location.
B2B Marketing Strategies That Drive Conversions often emphasize the importance of cybersecurity solutions for online businesses. Firewall as a Service (FWaaS) is a cloud-based firewall solution that can provide comprehensive security features for organizations of all sizes.
Benefits of FWaaS
FWaaS solutions present numerous benefits for businesses to take advantage of.
Easy to deploy & configure
Cloud-based firewalls are often simple to configure thanks to their single-panel interface, allowing organizations to set up modular tasks and select precisely which functions they wish to utilize.
Because third-party providers operate them, FWaaS solutions are much easier to deploy than NGFWs. There's no need to worry about investing time and resources into deploying on-premises hardware or software, as the provider will handle most of the setup.
All you need to do is tell them your requirements. So there's no need to worry if you're only operating a small, inexperienced team without so much as a data engineer certification between you when it comes to computing expertise.
Protect Remote Workers
With the increasing trend towards remote work, investing in cybersecurity solutions that protect network users wherever they're working from is increasingly important.
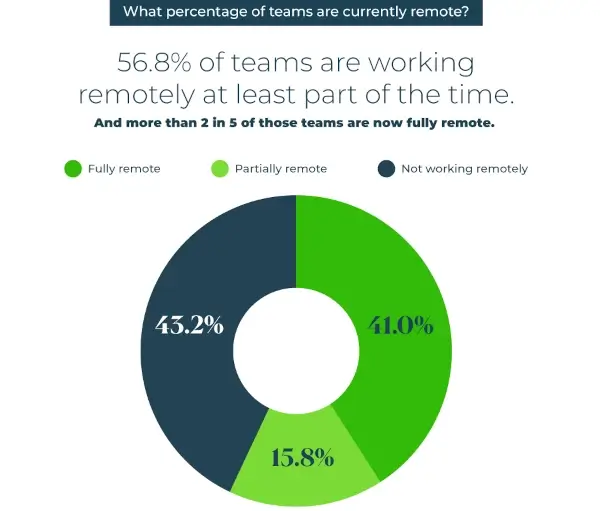
FWaaS solutions provide just this. By connecting remotely to the network, employees working from home or other off-site locations can access all the FWaaS benefits. This helps protect not only these employees and their devices but also the network at large.
Access to cloud resources such as CRM or unified communications platforms can also be protected using FWaaS solutions, so you're even protected while using VoIP with HubSpot integrations. With sensitive customer data being shared through channels such as these, it's imperative to employ security measures that keep the information confidential.
Scalability
FWaaS, like many cloud-based solutions, are inherently more scalable than its on-premises counterparts. This allows for the number of users, and the security utility, to increase as organizations grow and their individual needs change.
New users, or potentially even entire office locations, can be added to the FWaaS architecture, and protection can be extended to additional resources with minimum disruption to operational workflows. Acquiring and installing new hardware is unnecessary, as this will all be handled by the service provider.
Unified Security Policy
Using the cloud allows establishing a unified security policy and deploying it across an entire organization. This makes it easier for a business to defend against a broader range of threats at various vulnerable points.
Using a third-party service provider also means the hassle of sourcing, configuring, and managing various security features is handled for you. This helps reduce the likelihood of redundancy amongst security systems, where multiple measures guard against the same threat.
Flexibility
Using an FWaaS solution lets you decide how and when protections are applied. This means that processes can be configured to support the specific use cases of an organization, with different levels of protection being applied to other processes and assets if necessary.
This is especially useful in organizations that employ cloud-native development architectures or utilize other cloud-based services such as databases, content management systems, or other applications.
Visibility
FWaaS solutions give organizations real-time visibility of their network and its data. Multiple traffic sources can be viewed and controlled from one interface, making enforcing policies across the network easier.
Many FWaaS solutions generate detailed logs for each session and correlate events using advanced analytics. This provides greater insight into potential vulnerabilities and threats, especially when combined with a network vulnerability monitoring solution.
Why Should Organizations Use FWaaS
The increase in the number of cloud-based services that organizations use has, in turn, greatly increased the complexity of their networks. It's also expanded the list of potential security risks and challenges organizations face. This has resulted in the need for security measures to meet these challenges.
A perimeter-based network security approach is less practical when the network's perimeter constantly changes, requiring a more flexible solution. FWaaS can provide this.
FWaaS solutions also work fluidly with the ever-increasing number of cloud-based SaaS solutions organizations use while simultaneously protecting local resources.
Opting for an FWaaS solution allows organizations to customize the protections they receive and the features they can access. This makes it possible to tailor the service to an individual operation and its budget.
FWaaS Use Cases
Integrating FWaaS into cloud infrastructures can have numerous applications, suiting a range of businesses in various use cases.
- Secure VPN gateways: Organizations that employ a lot of remote workers, or have offices in numerous locations, can use FWaaS to establish secure access points to their network. Architecting single gateways is possible, saving the costs and time associated with managing multiple tunnels. This gives organizations peace of mind that their data and applications remain secure when connecting remotely to another computer or network through Virtual Network Computing (VNC). This allows for remote onboarding to be carried out securely, which can streamline the onboarding process and get remote workers up to speed quickly and effectively.
- Protection against threats: Organizations that handle sensitive data can customize their protections to defend against both known and unknown threats. Real-time deep packet inspection and state-full inspection capabilities help to provide a robust defense against web applications and incoming and outgoing data.
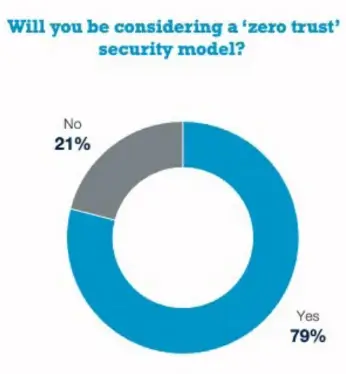
- Establish a zero-trust framework: A zero-trust network security framework is based on the philosophy that access should only be granted to a network if deemed completely necessary. Many organizations adopt this strategy to prevent malicious attacks and data breaches and provide secure network access. FWaaS solutions facilitate a zero-trust framework by bringing security policies to users at their endpoints, with customizable protections and access requirements.
Monitor Traffic Through the Cloud with FWaaS
FWaaS solutions help organizations protect their data, applications, and entire network. With the rise of cloud-based applications, FWaaS provides a flexible, scalable, and reliable solution as the needs of businesses change.
So whether you're analyzing customer data to identify consumer trends, chasing up leads from your cloud-based CRM software, or contacting clients from a VoIP communications solution, you can be confident that all the sensitive information you can access remains secure with a Firewall as a Service solution.


 Copyright 2000-2025, WebSitePulse. All rights reserved.
Copyright 2000-2025, WebSitePulse. All rights reserved.