 Less than half a decade ago to the present day, the word “hacker” was enough to send shudders down the spine of most system administrators of large businesses because those were the ones usually targeted. The much talked about denial-of-service attacks were incredibly effective when they were first used to hold businesses hostage. In fact, they sent CEOs scurrying to the company accounts to pay the demanded fee of these enterprising hackers, who only promised to suspend the DDoS attacks after their terms were met. Back then, it made sense, since a single day of downtime could (and still can) cost a corporation hundreds-of-thousands – if not millions of dollars, as well as untold loss of consumer confidence.
Less than half a decade ago to the present day, the word “hacker” was enough to send shudders down the spine of most system administrators of large businesses because those were the ones usually targeted. The much talked about denial-of-service attacks were incredibly effective when they were first used to hold businesses hostage. In fact, they sent CEOs scurrying to the company accounts to pay the demanded fee of these enterprising hackers, who only promised to suspend the DDoS attacks after their terms were met. Back then, it made sense, since a single day of downtime could (and still can) cost a corporation hundreds-of-thousands – if not millions of dollars, as well as untold loss of consumer confidence.
Extraordinary Hackers
The more sophisticated hackers use methods much more impressive than massive denial-of-service attacks to get into restricted systems. They do it for a variety of reasons, but most of all seems to be boredom and an itch to conquer the challenge. Consider these most famous cases:
Anonymous
 Image courtesy: www.wallpapersimg.com
Image courtesy: www.wallpapersimg.com
The most recent and elusive hacker in the news currently is Anonymous, which actually appears to be a loosely-connected group of so-called hacktivists. These guys (and girls; who knows?) first exploded on the scene in a DDoS attack on the Church of Scientology. Their purported aim was to discourage the alleged indoctrination of susceptible people by the religion concocted by late science fiction writer L. Ron Hubbard. Although it succeeded in blitzing the main site offline for a few hours, it wasn’t a sustained attack and appeared to be little more than a few hackers flexing their abilities. Nonetheless, the progenitors of Project Chanology, as the attack was dubbed, were unable to actually remain anonymous. Brian Thomas Mettenbrink and Dmitriy Guzner were both identified as the primary hackers and sentenced to a year in prison.
The Stuxnet Virus
 Roel Schouwenberg, of Kaspersky Lab, helped unravel Stuxnet.
Roel Schouwenberg, of Kaspersky Lab, helped unravel Stuxnet.
Image courtesy: spectrum.ieee.org
This next hacking attack ratchets up the stakes about as far as they can go: the Stuxnet virus. This was a potent piece of spyware that hacked the Iranian nuclear facilities in 2010, where it hijacked the industrial technology Iran’s Windows-based systems were using. Stuxnet is, to this day, easily one of the most sophisticated worms ever programmed, and the culprits are officially unknown. Various security experts who’ve analyzed the code in depth have suggested that both the United States and Israel had a hand to play in the manufacture of this cyber-attack on foreign soil.
Cyxymu
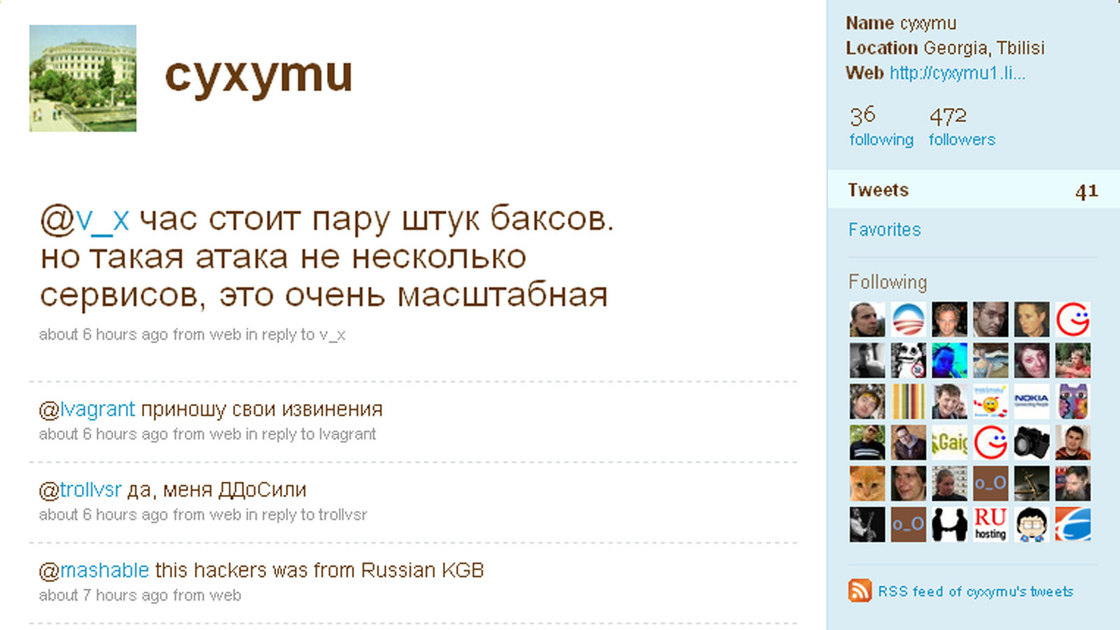 A Georgian man who goes by the name Cyxymu and is being called by some bloggers the first "digital refugee." This is a screenshot of his Twitter feed.
A Georgian man who goes by the name Cyxymu and is being called by some bloggers the first "digital refugee." This is a screenshot of his Twitter feed.
Image courtesy: www.npr.org
There’s been a virtual cyber war transpiring between Russia and the breakaway region of Georgia since 2008, with one of the most significant cyber –attacks being aimed at social network sites like Facebook, Twitter and LiveJournal. In 2009, a Georgian blogger with the screen name of Cyxymu. Apparently, Cyxymu was pontificating on the injustices carried out by Russia in the ongoing conflict and the Russian government decided to launch a massive DDoS attack; enough to actually shut down a service as well-protected as Twitter for a couple of hours. Although the Russian government never claimed credit for the attack, security experts from Facebook have fingered them as the culprit.
The Conficker Virus
Hackers are getting more sophisticated, forcing respondents to ratchet up their defenses. A recent computer worm has sprung up that is proving especially difficult to target and eradicate, given the continual updates to its programming that the unknown hackers are implementing. The Conficker virus is tailor-made to exploit none other than Microsoft’s Windows platform. First detected five years ago in 2008, it is still a potent virus today and regularly takes over many computers with its botnetfeatures, with new variants that are resistant to advanced extraction methods being pumped out by the unknown subjects. During its half-decade run so far, the Conficker worm has infected government, business and home workstations. Some of the more notable effects has been the grounding of aircraft, adverse effects in Canadian police information and millions of dollars’ worth of disruption in the operation of German institutions. The programmers are probably German or based on Germany but, to date, have remained hidden.
The Current State of Hacker Attacks
Fortunately, a brute-force method of attack like DDoS isn’t nearly as effective today, given the significant advances in programming in even the pedestrian web browser. There are a plethora of “gateway” advancements that even the most stripped-down ISP can use to minimize the effects of an impending DDoS attack. Furthermore, the real reason behind the fall of denial-of-service as an effective hacker tool is simply the size: computers can handle a lot more information now then even in the early 2000s. Regardless, the above hacking attacks have their place in history as some of the most significant to date and you can expect more sophisticated methods to manifest as the years roll by.


 Copyright 2000-2025, WebSitePulse. All rights reserved.
Copyright 2000-2025, WebSitePulse. All rights reserved.