
Data breaches and the threat of cybercriminals are unfortunate realities of our digital lives. Research conducted by tech firm IBM put the average cost of a corporate data breach at $4.24 million in 2021. This trend continues in both frequency and severity as we become more entangled in digital spaces (think virtual reality). There really is no better time to learn about the common causes of data breaches and how to prevent them.
What is a data breach?
A data breach can be broadly defined as any security violation that leads to unauthorized access to private data. This can manifest itself in many forms. For example, the data in question may belong to an individual or a wider company. It may lead to the permanent loss and destruction of that data or be sold or held for ransom for a financial incentive. In some cases, the data may be illegally viewed or leaked online for no financial gain whatsoever.
Cybercriminals employ many methods to carry out data breaches. This article will cover seven common types of data breaches in 2022 and what you must know to handle them.
7 common types of data breaches
External threats
Often, we see data breaches in the headlines as coming from 'outside' an organization, be it from a malicious attacker or group of attackers. Monitoring your organization's vulnerabilities can be difficult, so we've composed a list of common external threats.
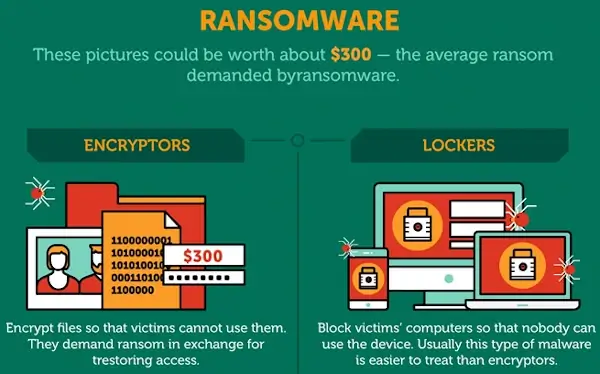
1. Ransomware attacks
The word 'ransomware' is a combination of 'ransom' and 'malware.' This gives us a good clue about the specific kind of data breach a ransomware attack is. Essentially, it involves using a type of harmful software to block and hold the victim's data to ransom.
For a ransomware attack to work, the victim's computer must first be infected with the attacker's malware. Often, phishing attempts are a way of propagating this attack. For example, you receive an email from a (supposedly) trusted source instructing you to download an attached file. Only that file is not what it seems; you are locked out of your account, and your files are held to ransom.
There are various varieties of attacks within the umbrella term 'ransomware.' The two most mainstream types are 'locker' and 'crypto' ransomware attacks, both of which operate similarly:
- Locker ransomware attacks work by locking the targeted user out of their computer or system, preventing them from accessing their personal files.
- On the other hand, crypto-ransomware attacks target and encrypt specific files (often high-value or sensitive data) to block a user's access to them.
Ransomware attacks that come from phishing sources can be prevented through education on cybersecurity practices. You may also consider regularly backing up data as a contingency for ransomware events.
2. Man-in-the-middle attacks
A man-in-the-middle (MITM) attack involves the interception of communications between two trusted parties. The attacker will first gain access to a line of communication, for example, an unsecured Wi-Fi network. From here, the hacker can access and collect any data that is transmitted through that network or system.
MITM attacks will usually target sensitive information, such as login credentials, files, or high-value personal/corporate data. Often, this type of attack exploits vulnerabilities in mobile networks and applications. Businesses and individuals can be targeted by a MITM attack, and it is often seen in the context of B2B or B2C communication.
Related to MITM attacks is the man-in-the-browser (MITB) attack. In this case, a cyber criminal will pose as a trusted third party, employee, or customer through spoof emails. Once this trust has been established, the attacker will deceitfully ask for access to sensitive data from the victim.
These types of attacks can be prevented by educating employees on cybersecurity practices. They should know only to communicate over secure, private networks. Additionally, they should remain vigilant of requests for information from unverified sources. Teaching data protection laws and their consequences will surely appreciate the severity of data breaches and hopefully prevent them.
3. XSS attacks
Cross-site-scripting (XSS) attacks are another widely used method by cybercriminals. It involves the 'injection' of a malicious script into the HTML body of an otherwise trusted website. When a victim accesses this infected webpage, their browser trusts the source and mistakenly allows it to execute the malicious script.
From here, the malicious script can prey on the victim's browser data. Not only does the attacker have access to confidential information such as website cookies or session data, but they can perform more advanced attacks. For example, they may log user keystrokes or take screenshots of sensitive web pages.
One of the best lines of defense against an XSS attack is the use of a web application firewall. These firewalls can identify and block malicious activity before a script has a chance to execute. They can also warn your IT department (or the user) about attempted attacks, allowing discovery and awareness of vulnerabilities.
4. SQL injection attacks
Structure Query Language (SQL) is a domain-specific programming language often used to manage Internet databases. It follows then that a SQL injection attack involves the addition of a malicious script into a database's SQL. These attacks are particularly effective as they confer admin-level privileges onto the attacker, handing them complete control over that web-based application.
However, they are also a lengthy and complicated process to set up. Firstly, the hacker must identify a security vulnerability within the SQL code of an application's software. From here, SQL statements must be written and entered to command specific actions within that compromised system. For instance, the attacker may command the database to 'dump' its content elsewhere on the Internet for the attacker's use.
The best defense against a SQL injection attack is to close any vulnerabilities within a database's SQL. Regular security audits by external 'ethical hackers' may help identify weaknesses before exploiting them. One trick is to limit the permissions available on the web application so that if infected, the scope of the attack is deeply diminished.
Another consideration is using an open-source software platform to manage big data applications, such as Apache Hadoop. What is Hadoop? It works by distributing data sets into smaller workloads to run in parallel. This decreases the risk of a severe attack by spreading privileges across multiple nodes, preventing a serious single source of the attack.
5. Physical attacks
Concluding our list of external cybersecurity threats is the risk of physical attack. On one hand, this can mean the literal physical theft of a device belonging to an individual or company. Once an attacker has physical access to a stolen device such as a smartphone or laptop, it is very hard to stop them from accessing the confidential data within.
On the other hand, a physical attack may manifest itself as the physical insertion of a device onto a secure network. For example, a USB drive with malicious software is injected into company computers for widespread infection.
Regardless of its specific tactic, the risk of physical attack highlights the need for attentiveness within an organization's ranks. Basic cybersecurity practices should be taught and enforced in your company. For example, valuable devices should always be kept on the person. If not possible, they should be protected with a strong password and logged out to prevent manipulation. Physical server rooms should remain locked and restricted to only authorized individuals. Additionally, camera systems may deter opportunistic breaches or help identify the source of the attack.

Internal threats
In addition to the external threats outlined above, security breaches may arise within the affected organization. This highlights the need for vigilance and awareness of cybersecurity from both an external and internal perspective.
6. Insider sabotage
No organization wants to think that a cyber attack and resulting data breach could come from one of their own employees. However, this wishful thinking means that internal breaches often slip through undetected, with that source of breach remaining unaccountable for their actions. As such, companies need to protect essential data from any potential source of an attack, external or internal.
These types of data breaches can be prevented by limiting users' permissions on a network to what is simply necessary for their role. A UEBA cybersecurity solution may also help identify unusual behavior from employees, e.g., logging on at strange hours or accessing different files than usual.
7. Human error
The final source of a data security breach we will cover today is basic human error. Human error can arguably apply to many types of data breaches on this list, such as attempted social engineering attacks. Phishing attempts rely on the erroneous trust of a malicious attacker, for example.
We all make mistakes in our everyday jobs, and it is simply unrealistic to expect that your employees will have a perfect cybersecurity track record. The worst effects of human error can be mitigated by educating employees on safer practices and safer platforms, like Apache Hive, for example. What is an apache hive? It's a data storage solution that provides an open-source, secure metadata store for an organization's datasets.

Conclusion
To conclude, there are many potential sources of a data breach, both internal and external to an organization. Companies and individuals must remain vigilant of best cybersecurity practices to prevent attacks and security breaches. When it comes to protecting high-value data, businesses may consider looking at comprehensive cybersecurity packages to identify and prevent sources of attack.


 Copyright 2000-2025, WebSitePulse. All rights reserved.
Copyright 2000-2025, WebSitePulse. All rights reserved.