
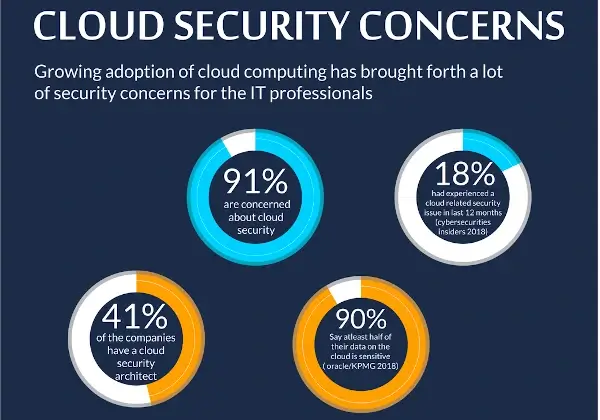
The early days of cloud computing saw people subject it to severe scrutiny. The main talking point revolved around its security and the ability of infrastructure providers to keep it secure.
Regardless of the doubts, more businesses are migrating to the cloud. That's mainly because leading cloud service providers have consistently improved and upgraded their processes to secure their networks.
However, even with years of improvement, the old fears remain. For example, Statista reported that approximately 55% of cloud users had experienced data encryption issues.
Cloud security is a huge deal and continues to evolve with time. Hence, it's becoming a niche for innovation and various data protection strategies. Below are some of the emerging cloud security trends you should note for 2022.
What's Cloud Security and How Does It Work?
Cloud security is a complex mix of technology, protocols, and best practices designed to protect the cloud computing environment. Of course, it also safeguards applications running in the cloud and data storage.
Cloud security is more technical than the simplistic definition above paints it. With internet protocols like domain names, simply Googling how much a domain name costs can provide definitive answers. The reality isn't the same for cloud security.
First, you need a deep understanding of cloud computing to handle cloud security. Not only that, but you also need adequate knowledge of cloud systems and components that require appropriate management in the process.
Backend provisions against cloud computing vulnerabilities largely rest with the service providers. Therefore, it's important to remain highly selective of providers who deliver cloud solution services.
First, always hold out for security-conscious service providers. Then, you should do your part by focusing on proper service configuration and safe-use practices.
The full scope of cloud security covers the following systems, which you can apply as necessary.
- Computer visualization frameworks – Includes virtual machines, host machines (like domain names NZ), guest machines, and other related software.
- Physical Networks – Includes electrical power, routers, cabling, and even climate control.
- Data Storage – Applies to cloud databases and physical-digital storage such as hard drives.
- Data Servers – Includes core network computing software and hardware systems.
- Runtown environments – You can also use cloud security for executing and maintaining a running program.
- Operating systems – Cloud security protects operating systems and software that houses other applications.
- Middleware – Cloud security also applies to middleware such as Application Programming Interface (API) management systems.
- Applications – Cloud security covers traditional software services such as email problems, social media, and productivity suites.
- End-User hardware – Finally, you can use cloud encryption to safeguard your computer, mobile phones, and Internet of things items.
2022 Emerging Trends in Cloud Security
Cloud security covers a wide range of functionality and coverage. Hence, available solutions are numerous, and new ones keep popping up to fulfill continuous security monitoring.
Let's examine some cloud security trends to look forward to in the remainder of 2022.
SDLC and DevSecOps Within the Cloud
More businesses are adopting DevOps as a viable Software Development Life Cycle (SDLC) framework. Its efficiencies allow companies to develop effective software programs without risk or waste.
Then again, adopting DevOps creates a new requirement for the organizations using it. For example, incorporating DevOps into your systems will necessitate you to get automation and infrastructure management solutions.
Cloud services provide the most reliable aid in this instance. In addition, you can use cloud solutions to secure and quicken the integration process.
The combination of security task automation and the SDLC process gives birth to DevSecOps. But this mix does not take away the people's roles in the process. So, the new trend will involve people using cloud technology to ensure security is not only at the top layer but integrates seamlessly with the system.
Then again, cloud computing relating to SDLC will require that all security measures satisfy all aspects of the SDLC pipeline. The standards must also safeguard the infrastructure data and its environment. As a result, you can expect DevSecOps to grow and improve rapidly to match these requirements.
Centralized Platforms for Multi-Cloud Security Proliferating the Market
Most companies employ multiple cloud solutions simultaneously. Flexera's 2021 State of the Cloud Report shows that 92% of enterprises use multi-cloud strategies.
Managing these services may be challenging and lead to inefficiency in some systems. Therefore, most organizations are actively looking for arrangements to secure each cloud component as a unit.
Emerging cloud security trends show a need for a centralized way to apply security controls and policies on multiple systems across the board. An existing system that provides a semblance of such services is a Cloud Security Access Broker (CASB).
The CASB is a software buffering the gap between cloud apps and cloud service users. It monitors all activities in the space and enforces security policies.

Organizations Employing More Pre-Cloud Data Protection Measures
We mentioned earlier that the old fears regarding the security of cloud solutions against data breaches are still prevalent. A passive campaign is ongoing to force organizations to secure data garnered from users before pushing them to the cloud to address these concerns.
Organizations have been reasonably casual with how they transfer data to cloud storage. They often merely push the data to the cloud and let the cloud protection mechanisms take care of the rest. However, since cloud migration has become mainstream, the process's vulnerabilities are becoming more apparent.
2022 cloud security trends reveal a clamor for data encryption before cloud storage. Stakeholders believe controlling data at the record level is crucial to data safety.
Then again, new legal and regulatory constraints necessitate organizations to encrypt cloud data. Generally, the pre-cloud storage data encryption trend is increasing the adoption of Bring Your Own Key policies. BYOK solutions enable data owners to restrict access to information from individual users without proper authorization.
Growing Priority on Access Control and Identity
Tokenization and encryption have done an excellent job regarding identity and access control. However, organizations are more particular about critical management measures.
A closer look at key cloud security trends shows companies are adopting the Zero-trust model. This model restricts access to resources, services, and data to an "as-needed" basis.
Zero-trust model pairs seamlessly with cloud solutions. For example, companies get to save money by rolling out the zero-trust model while creating services in the cloud. It also helps them mitigate risks and reduce time spent rectifying avoidable issues (pretty much like a model risk management system but for cloud security).
Then again, a system's security starts with the users. So, organizations can up their security measures by identifying high-risk users and fortifying possible attack points.
To address the growing attention on identity and access control for cloud solutions, cloud service providers are now integrating unique identity management features into their environments. They're also using machine-language-based analysis to educate users about the "who can access what" part of their infrastructure. Lastly, the systems also advise the users on how to manage permissions.
SASE Frameworks Bringing Security and Access Close to Users
The Secure Access Service Edge (SASE) framework is a high-quality product that enables fast and secure cloud adoption for end-users. You can view SASE as a VPN with cloud privileges and capabilities. The solution ensures users and devices can securely access data, applications, and services anywhere, anytime.
The pandemic contributed to the SASE system's growth by encouraging users to adopt secure cloud solutions while working from home. Being a cloud-native application, SASE pushes network access and security to users.
Furthermore, users can scale a cloud service like SASE more quickly than a VPN gateway. So, it makes sense for remote workers, as it gives them access to cloud security provisions right where they are.
In addition, SASE is faster and more efficient than alternative technologies. Nonetheless, users can still connect to corporate networks available at cloud data centers to use enterprise software. But that allows IT admins to monitor access and control the network.
Overall, SASE is gaining widespread adoption by companies and individuals seeking more secure ways to use the net. So with SASE, you can effortlessly search for available Australian domain names from the U.S without needing a VPN or revealing your location.
Cloud-Based Security Will Continue to Thrive
Despite the doubts surrounding its efficiency, several companies are still signing up for cloud-based security. The reason for the growth is apparent. Cloud security solutions combine economies of scale, lower service costs, greater threat intelligence, and easier compliance with existing regulations and standards.
Different approaches are practical for securing cloud environments. Hence, you should expect an improvement in most existing cloud security strategies. But more than that, you should anticipate several innovative solutions going forward.
More than ever, providers are experimenting with the prospects and extent of cloud security systems. Stay informed!


 Copyright 2000-2025, WebSitePulse. All rights reserved.
Copyright 2000-2025, WebSitePulse. All rights reserved.