
API is short for Application Programming Interface. The software-to-software interface provides a secure and standardized way for systems to work with each other. API security means implementing practices that protect APIs from malicious attacks and data theft.
Thanks to APIs, applications can deliver the information or functionality requested without user intervention. This means our everyday digital experiences remain virtually effortless.
As comprehensive API traffic management systems are widely used on the web, they are also very attractive to hackers. Cybercriminals continue to work on new ways to hack security policies and exploit information stored on your servers. The lack of proper API security measures leaves the window open for data breaches.
In this article, we'll cover the API security best practices that enable companies to protect sensitive data. Implementing and maintaining these will ensure your company can enjoy the benefits of API technology. At the same time, you can protect your business' and clients' sensitive data.
Let's dive in.
1. Leverage token-based authentication
One of the API security best practices in protecting sensitive data includes using access tokens for authentication. A basic authentication token is a string of characters used as a unique identifier for a user.
The API has to match the token sent with the request with the one stored in the database. If the token doesn't match, the system doesn't authenticate the attempt and rejects the request. As a result, tokens help companies with access control and ensure that only trusted users can enter the company's resources. It can also help with reducing accidental exposure.
The OAuth protocol is a common practice used for API user authentication. OAuth was initially created for social logins. It allows users to log into third-party apps with passwords without disclosing the combinations.
For example, with OAuth, you can use your Google password to log in to a third-party website like Facebook without requiring Facebook to store your password. For API administrators, OAuth allows authentication tokens to chosen third-party services.
Administrators can set rules for custom access that determine which API requests will be allowed based on the request's source.
Website security should be the prime aspect of any online business strategy. Any website can be targeted by third parties trying to collect sensitive data. That's why it's important to scan your servers and firewalls regularly.
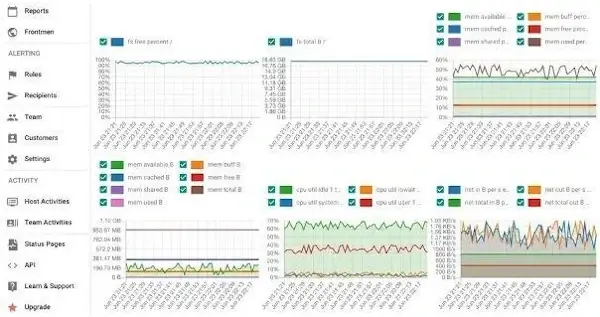
Reports like the one shown above will help you identify any issues and understand the system's resource usage for a smooth operation. You'll also get information and recommendations on how to make your systems and servers more secure.
2. Encrypt traffic
With growing concerns around API security, encryption of sensitive data must be businesses' top priority. All data in transit, especially sensitive ones, should be encrypted with security policies such as Transport Layer Security (TLS). This way, in case of criminal activity, the requests or responses are useless to the hacker without the proper decryption method.
Transport Layer Security provides what we can call a "secure channel" between two parties. TLS requires setting up rules and a mutual encryption scheme for both parties involved. The parties then use the exact encryption details for each message they exchange.
Today, TLS protocol is standard across the web. URLs that begin with HTTPS, Hyper Text Transfer Protocol Secure, are protected with TLS. It keeps an internet connection private and checks the data sent between two parties is encrypted and unmodified. This could be between a server and a server or a server and a client. It is essential to monitor your TLS certificate for expiration and validity.
So, for example, a hacker trying to steal your customer's credit card data from your eCommerce will be unable to read your data or modify it, thanks to TLS.
Today's B2B and B2C clients are especially concerned about how start-up companies handle and store data. People want to know if companies use certified solutions with security measures. So if you're a new business owner thinking of putting up a website as part of your marketing plan for SaaS or retail, discuss data security measures first.
3. Place your API behind a gateway
Placing your API behind a gateway is another from the list of API security best practices you should follow. Choosing a good gateway will allow companies to authenticate traffic. The tool can also help with an API audit.
This is especially important for companies using microservices to deal with clients rather than one monolith application. Below is an image illustrating some of the microservices a company can use. Those services are placed behind one service layer- the API gateway.
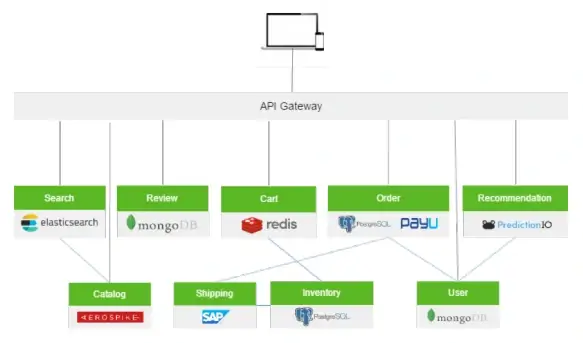
API gateways are software patterns. They centralize traffic features and apply them to every request. The features set can relate to security, like limiting the rate, logging, or blocking malicious users. On the other hand, business-related features, like path and headers rewriting, or gathering business metrics, are more practical features.
Without a gateway, API admins have to set up each endpoint with these features one by one. So, an API gateway makes it easier to add or fix the features.
API Gateway also helps introduce message security between internal services. Your internal services can become more secure with, for example, the messages going back and forth between the services being encrypted.
Google Cloud offers its API Gateway to create, secure, and monitor APIs for its serverless back ends, including Cloud Functions, Cloud Run, and App Engine.
4. Set up a protocol to validate requests
Sometimes, a perfectly valid source may be a hacking attempt. That's why APIs need a protocol to determine if a request is friendly, friendly but invalid, or harmful.
With a protocol in place, an API request is only processed after passing a thorough validation check. In case of failure, the system rejects the request. So, after verifying the requester's identity, API will grant access to only the authorized resources and methods.
For example, let's say a user is authorized to access an API. However, they aren't allowed to input any data into the database through the POST method. So in case, they make an attempt to do so, the system will reject their request.
This is especially relevant for remote teams. Your employees may use an online communication platform, an issue-tracking tool, or project management software daily. Disregarding security controls could lead to serious security threats.
5. Place rate limits on your APIs
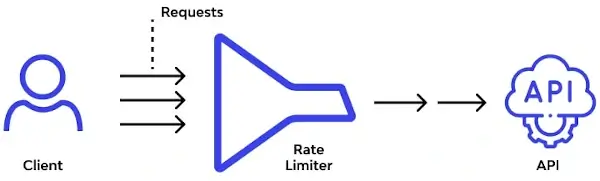
As the usage of API has been increasing, it's becoming a popular target for cyber attacks. To avoid various types of attacks and security issues that have an impact on performance and safety, you should place rate limits on your APIs.
Rate limiting determines how and how often your API can be called. It can also throttle connections which helps balance access with availability.
Every user should be allowed to access data through the API at a set rate. This practice reduces the risk of authorized team members misusing their access or hijacking their identity. Such events can lead to severe data breaches.
For example, let's assume someone needs to connect to the company's API to validate new users. If the person executes your API at a rate of 1,000 calls per second, it could mean the API is being abused to harvest data. Limiting users' access to one call per second would ensure only genuine calls go out.
Rate limiting is flexible; you can adjust it to cover different users and roles. So, different rate limits can be implemented for different API calls.
In Closing
If your company follows API security best practices, it can sufficiently safeguard APIs and eliminate unwanted behavior. This is important because an API security mistake can lead to severe data breaches.
You can ensure your business's safety if you encrypt traffic and implement token-based authorization. You should validate all API requests and set user rate limits. You should also place your API behind the gateway to keep security threats away. Network vulnerability monitoring services can help businesses detect such security issues.
Now that you've learned the API security best practices, you can implement them and ensure high-standard API security in your organization.


 Copyright 2000-2025, WebSitePulse. All rights reserved.
Copyright 2000-2025, WebSitePulse. All rights reserved.